GitOps Project – End-to-End CI/CD with AWS, Terraform, GitHub Actions, and Helm
Tech Stack
- Version Control and CI/CD: GitHub, GitHub Actions
- Infrastructure as Code: Terraform (AWS VPC and EKS modules)
- Cloud Provider: AWS (VPC, EKS, ECR, S3, IAM)
- Application Development: Java application built with Maven and Checkstyle validation
- Containerization and Orchestration: Docker, Kubernetes, Helm
- Code Quality and Analysis: SonarCloud, Maven Checkstyle
Project Goal
The main goal of this project was to implement GitOps principles by automating both infrastructure provisioning and application deployment on AWS. All changes are tracked and managed through Git repositories, and workflows are executed by GitHub Actions, ensuring consistency, traceability, and elimination of manual operations in the AWS console.
Project Description
This project demonstrates a complete GitOps workflow with two separate GitHub repositories: one dedicated to infrastructure code and the other to application code. Infrastructure provisioning is handled with Terraform, while application build and deployment are fully automated with Maven, SonarCloud, Docker, Amazon ECR, and Helm on Kubernetes (EKS).
The infrastructure repository provisions a complete AWS environment, including a VPC, EKS cluster, and networking components, with workflows ensuring changes are validated in staging and only applied in production after approval. The application repository automates testing, builds container images, pushes them to ECR, and deploys them to the Kubernetes cluster using Helm charts.
Architecture Overview
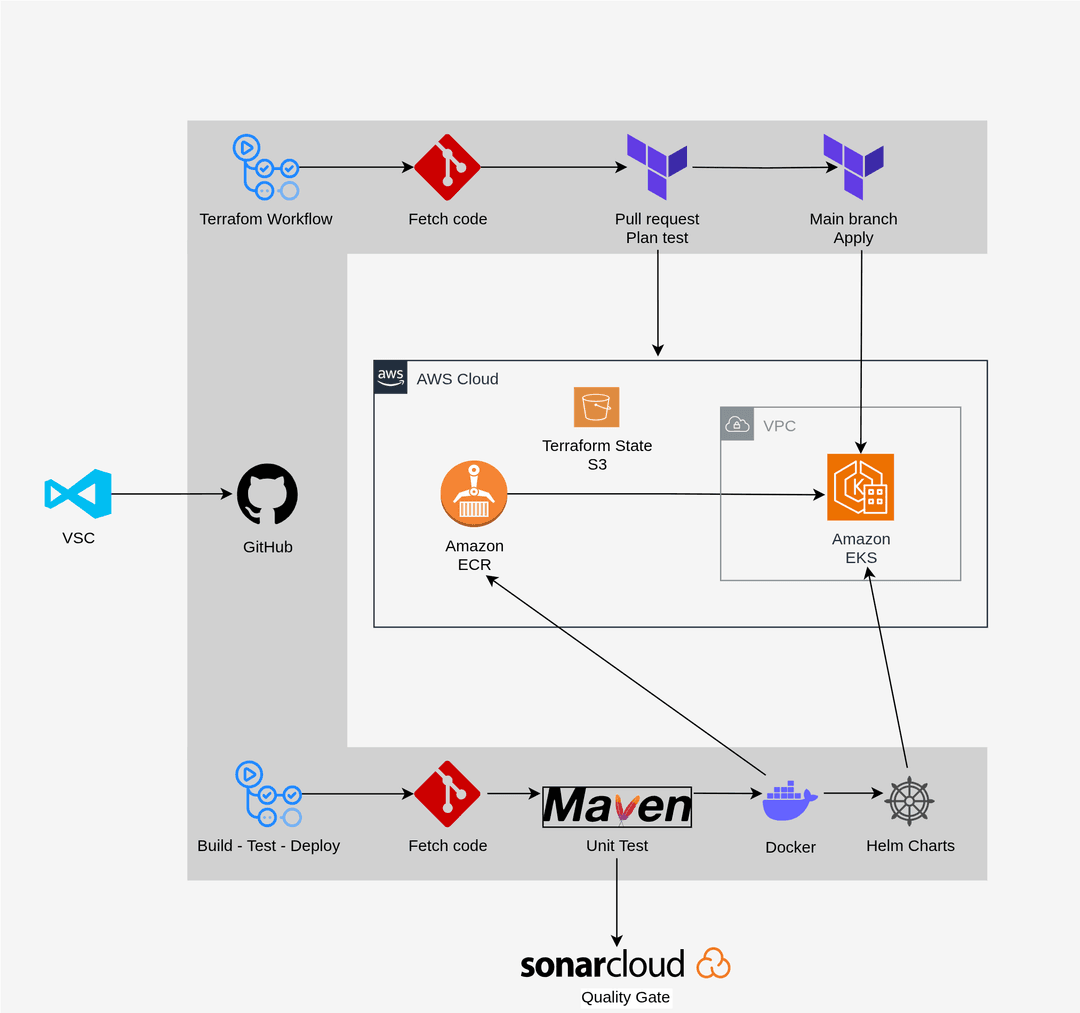
- Infrastructure Repository (iac-vprofile)
- Contains Terraform code for VPC and EKS provisioning.
- GitHub Actions workflow validates code (terraform validate, terraform plan) on the staging branch.
- Approved pull requests to the main branch trigger terraform apply, creating or updating resources in AWS.
- An NGINX Ingress Controller is installed automatically after cluster creation.
- Application Repository (vprofile-action)
- Contains application source code, Dockerfile, Kubernetes manifests, and Helm charts.
- GitHub Actions workflow executes Maven tests, Checkstyle validation, and SonarCloud analysis.
- Successful builds create Docker images tagged as latest and with a unique run number, pushed to Amazon ECR.
- Helm charts deploy the application to the EKS cluster with dynamic values for image name and tag.
- Ingress rules expose the application externally via a DNS record pointing to the AWS load balancer created by the Ingress Controller.
Implementation Details
Infrastructure
- Terraform modules: Official AWS VPC and EKS modules.
- State management: Remote backend in S3 to ensure centralized state management.
- Cluster setup: EKS with two managed node groups (t3.small instances) and autoscaling.
- Ingress: NGINX Ingress Controller installed through GitHub Actions to handle external access.
Application
- Build and validation: Maven tests, Checkstyle rules, and SonarCloud analysis with quality gates.
- Image creation: Docker image built on each change, tagged consistently, and pushed to Amazon ECR.
- Helm deployment: Manifests parameterized with Helm values for image and tag, allowing dynamic updates.
- Workflow sequence:
- Testing job (Maven, SonarCloud).
- Build and publish job (Docker image to ECR).
- Deployment job (Helm release to EKS, authenticated with AWS and Kubernetes secrets).
Access and Routing
- Ingress configured to map vprofile.<domain> to the application service running inside the cluster.
- DNS CNAME record configured to point the subdomain to the AWS load balancer.
Future Improvements
- Extend the solution with monitoring and observability (Prometheus and Grafana).
- Integrate secrets management with AWS Secrets Manager or HashiCorp Vault.
- Replace administrator IAM credentials with least-privilege roles for GitHub Actions.
- Implement multiple environments (staging, QA, production) for more realistic workflows.
Outcomes
- Successful implementation of GitOps principles across infrastructure and application layers.
- Full automation of validation, approval, and deployment processes.
- Clear separation of responsibilities through dedicated repositories for infrastructure and application.
- Consistent, reproducible, and traceable deployments on AWS EKS.
- Practical demonstration of how GitOps prevents drift and enforces accountability in modern DevOps workflows.